Network management:Applications of Cryptography to Security
Applications of Cryptography to Security
• The science and art of manipulating messages to make them secure is called
cryptography.
• Original message to be transformed is called plaintext.
• Resulting message after the transformation is called ciphertext.
• Process of converting plaintext to ciphertext is called encryption
• Reverse process is called decryption
• Algorithm used for encryption and decryption is called Cipher.
Ex : Substitution and Transposition Ciphers Substitution Cipher
• Substitution ciphers are a common technique for altering messages in games and puzzles.
• Each letter of the alphabet is mapped into another letter.
a b c d e f g h i j k l m n o p q r s t u v w x y z
z y x w v u t s r q p o n m l k j i h g f e d c b a
Transposition Cipher :
• Here the order in which the letters of the message appear is altered.
• Substitution and transposition techniques are easily broken.
Cryptographic method must meet several requirements
1. It must be easy to implement
2. It should be deployable on large scale
3. It must provide security to all of its users.
4. It should prevent an attacker from deriving the key even when a large sample of the plaintext and corresponding ciphertext is known
Cryptography is best known as a way of keeping the contents of a message secret. Confidentiality of network communications, for example, is of great importance for e- commerce and other network applications.. In particular, cryptography allows the network business and customer to verify the authenticity and integrity of their transactions. If the trend to a global electronic marketplace continues, better cryptographic techniques will have to be developed to protect business transactions.
Cryptography is best known as a way of keeping the contents of a message secret. Confidentiality of network communications, for example, is of great importance for e- commerce and other network applications.. In particular, cryptography allows the network business and customer to verify the authenticity and integrity of their transactions. If the trend to a global electronic marketplace continues, better cryptographic techniques will have to be developed to protect business transactions.
Sensitive information sent over an open network may be scrambled into a form that cannot be understood by a hacker or eavesdropper. This is done using a mathematical formula, known as an encryption algorithm, which transforms the bits of the message into an unintelligible form. The intended recipient has a decryption algorithm for extracting the original message. There are many examples of information on open networks, which need to be protected in this way, for instance, bank account details, credit card transactions, or confidential health or tax records.
Symmetric-key cryptography
An encryption system in which the sender and receiver of a message share a single, common key that is used to encrypt and decrypt the message.
Symmetric-key systems are simpler and faster, but their main drawback is that the two parties must somehow exchange the key in a secure way. Public-key encryption avoids this problem because the public key can be distributed in a non-secure way, and the private key is never transmitted.
Symmetric-key cryptography is sometimes called secret-key cryptography. The most popular symmetric-key system is the Data Encryption Standard (DES).
The disadvantage of symmetric cryptography is that it presumes two parties have agreed on a key and been able to exchange that key in a secure manner prior to communication.
r is some random number sent by sender
Ek(r) is encryption of random number r
r’ is some random number sent by receiver
Ek(r’) is encryption of random number r
Before two parties can send information securely, they must first exchange a secret key. how can the two parties exchange a key secretly before they can communicate in secret? Even if the sender and receiver found a channel that they believed to be secure, in the past there has been no way to test the secrecy of each key. Quantum cryptography solves this problem. It allows the sender and receiver to test and guarantee the secrecy of each individual key.
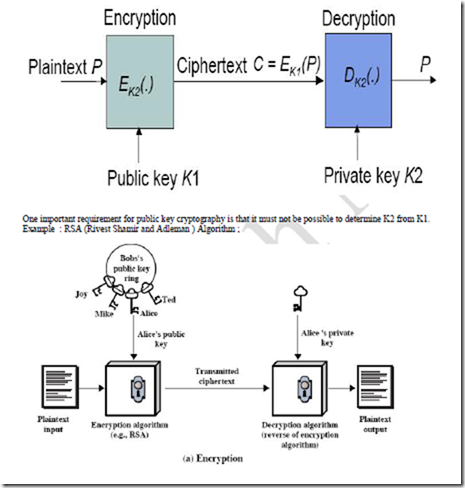
Public-key cryptography
A cryptographic system that uses two keys -- a public key known to everyone and a private or secret key known only to the recipient of the message.
When John wants to send a secure message to Jane, he uses Jane's public key to encrypt the message. Jane then uses her private key to decrypt it.
An important element to the public key system is that the public and private keys are related in such a way that only the public key can be used to encrypt messages and only the corresponding private key can be used to decrypt them. Moreover, it is virtually impossible to deduce the private key if you know the public key.
Public key cryptography was invented in 1976 by Whitfield Diffie and Martin Hellman.
For this reason, it is sometime called Diffie-Hellman encryption.
It is also called asymmetric encryption because it uses two keys instead of one key (symmetric encryption).
Key Distribution center (KDC)
Secret key systems require every pair of users to share a separate key.
Consequently the number of keys grow as the square of the number of users making these systems unfeasible for large scale use.
This problem can be addresses through the introduction of KDC
For example, assume the KDC shares a different secret key with each user. Han Solo contacts the KDC with a request to communicate with Luke Skywalker (1). The KDC creates a symmetric secret session key, encrypts it with the secret key shared with Han (2) and transmits the key to Han (3). Next the KDC encrypts the secret session key with the secret key shared with Luke (2), then transmits the message to Luke (3). Luke and Han now have the secret session key and commence the communication. Note that changing session keys enhances the security of the communications. The message from the KDC to Luke and Han will normally specify the algorithm (including padding scheme, etceteras) in addition to the session key.
Certification Authority (CA)
• Public key systems require only one pair of keys per user, but they still face the problem of how public key are to be distributed.
• The public keys must be certified somehow.
• One approach to address this problem is to establish a Certification Authority (CA).
• To issue certificates that consist of signed message stating the name of given user, his or her public key, s serial number identifying the certificate and an expiration date
Diffie-Hellman key exchange
In 1976, Whitfield Diffie and Martin Hellman published their method for public exchange of a secret key. This became known as Diffie-Hellman key exchange, and was the first known way to distribute keys for secure communication.
The exchange method relies on simple mathematical fact: (xy)z = (xz)y
Here’s how Diffie-Hellman key exchange works:
· Alice and Bob agree on a long prime number, p, and a base g. The base, g, doesn’t
need to be large; it is normally 2 or 5.
· Alice creates a long prime number, a, which is her private key. She calculates A = ga mod p. She sends A to Bob.
· Bob creates his own long prime number, b, which is his private key. He calculates B
= gb mod p. He sends B to Alice.
· Alice gets B from Bob, and calculates the shared key: K = Ba mod p.
· Bob gets A from Alice, and calculates the same shared key: K = Ab mod p.
· Now, Alice and Bob have calculated respectively K = (ga)b mod p and K = (gb)a mod
p. From the first formula above, we know these are actually the same value: the shared key which Alice and Bob will use to communicate securely.

The required exponentials need many multiplications for large prime numbers p It could produce a heavy computational burden on a machine and result in Denial Of Service to legitimate Client.
Man in the Middle attack in Diffie-Hellman key exchange
In Below figure
1. Alice choose x, calculates R1= gxmod p, and sends R1 to Bob.
2. Eve, the intruder, intercepts R1. She chosses Z, calculates R2= gzmod p and sends R2 to both Alice and Bob.
3. Bob chooses y, calculates R3= gymod p, and sends R3 to Alice; R3 is intercepted by Eve and never reaches Alice.
4. Alice and Eve calculate K1= gxzmod p, which becomes a shared key between Alice and Eve.Alice , however, thinks that it is a key shared between Bob and herself.
5. Eve ad Bob calculate K2= gzy mod p. which becomes a shared ey between Eve and Bob. Bob, however, thinks that it is a key shared between Alice and himself.
IPsec
IPsec (Internet Protocol Security) is a framework for a set of protocols for security at the network or packet processing layer of network communication.
Earlier security approaches have inserted security at the application layer of the communications model.
IPsec is said to be especially useful for implementing virtual private networks and for remote user access through dial-up connection to private networks.
A big advantage of IPsec is that security arrangements can be handled without requiring changes to individual user computers.
Cisco has been a leader in proposing IPsec as a standard (or combination of standards and technologies) and has included support for it in its network routers.
IPsec provides two choices of security service: Authentication Header (AH), which essentially allows authentication of the sender of data, and Encapsulating Security Payload (ESP), which supports both authentication of the sender and encryption of data as well.
The specific information associated with each of these services is inserted into the packet in a header that follows the IP packet header.
There are two modes of IPsec operation:
Transport mode
In transport mode, only the payload (the data you transfer) of the IP packet is encrypted and/or authenticated.
Tunnel mode
In tunnel mode, the entire IP packet (data and IP header) is encrypted and/or authenticated.
Authentication Header (AH)
AH is a member of the IPsec protocol suite.
AH is intended to guarantee connectionless integrity and data origin authentication of IP packets.
AH protects the IP payload and all header fields of an IP datagram except for mutable fields (i.e. those that might be altered in transit).
In IPv4, mutable (and therefore unauthenticated) IP header fields include DSCP/TOS, Flags, Fragment Offset, TTL and Header Checksum.
AH operates directly on top of IP, using IP protocol number 51.
The following AH packet diagram shows how an AH packet is constructed and interpreted:
1. An authentication header is added to the payload with the authentication data field set to zero.
2. Padding may be added to make the total length even for a particular hashing algorithm. and it tells which hasing algorithm is used to calculate Authentication data.
3. Hashing is based on the total packet. However, only those fields of the IP header that do not change during transmission are included in the calculation of the message digest (authentication data).
4. The authentication data are inserted in the authentication header.
5. The IP header is added after the value of the protocol field is changed to 51. A brief description of each field follows:
Next header. The 8-bit next-header field defines the type of payload carried by the IP datagram (such as TCP, UDP, ICMP, or OSPF). It has the same function as the protocol field in the IP header before encapsulation. In other words, the process copies the value of the protocol field in the IP datagram to this field. The value of the protocol field in the new IP datagram is now set to 51 to show that the packet carries an authentication header.
Payload length. The name of this 8-bit field is misleading. It does not define the length of the payload; it defines the length of the authentication header in 4-byte multiples, but it does not include the first 8 bytes.
Security parameter index. The 32-bit security parameter index (SPI) field plays the role of a virtual-circuit identifier and is the same for all packets sent during a connection called a security association (discussed later).
Sequence number. A 32-bit sequence number provides ordering information for a sequence of datagrams. The sequence numbers prevent a playback. Note that the
sequence number is not repeated even if a packet is retransmitted. A sequence number does not wrap around after it reaches 232; a new connection must be established.
Authentication data. Finally, the authentication data field is the result of applying a hash function to the entire IP datagram except for the fields that are changed during transit (e.g., time-to-live).
The AH Protocol provides source authentication and data integrity, but not privacy.










Comments
Post a Comment