TCP/IP-1 part1
UNIT III- TCP/IP-1
TCP/IP Architecture
- The TCP/IP protocol suite usually refers not only to the two most well-known protocols called TCP and IP but also to other related protocols such as UDP, ICMP, HTTP, TELNET and FTP.
- Basic structure of TCP/IP protocol suite is shown in above figure.
- Protocol data unit (PDU) exchanged between peer TCP protocols is called segments.
- Protocol data unit (PDU) exchanged between peer UDP protocols is called datagrams.
- Protocol data unit (PDU) exchanged between peer IP protocols is called packets.
- In the above figure an HTTP GET command is passed to the TCP layer, which encapsulates the message into a TCP segment.
- The segment header contains an ephemeral port number for the client process and well known port 80 for HTTP server process.
- The TCP segment is passed to IP layer where it is encapsulated in an IP packet.
- The IP packet contains source and destination network address.
- IP packet is then passed through network interface and encapsulated into PDU of underlying network.
- In the network interface, the IP packet is encapsulated into an Ethernet frame, which contains physical addresses that identify the physical endpoints for the Ethernet sender and receiver.
· IP packets transfer information across Internet
· Host A IP → router→ router…→ router→ Host B IP
· IP layer in each router determines next hop (router)
· Network interfaces transfer IP packets across networks
· Internet Names
· Each host has a unique name
o Independent of physical location
o Domain Name will facilitates memorization by humans
· Host Name
o Name given to host computer
· User Name
o Name assigned to user
Internet Addresses
- Each host has globally unique logical 32 bit IP address
- Separate address for each physical connection to a network
- Routing decision is done based on destination IP address
- IP address has two parts:
- netid and hostid
- lnetid unique
- netid facilitates routing
- l Dotted Decimal Notation is used for representation:
Ex: - int1.int2.int3.int4
128.100.10.13
DNS(Domain Name Service) resolves IP name to IP address
Physical Addresses
· LANs (and other networks) assign physical addresses to the physical attachment to the network
· The network uses its own address to transfer packets or frames to the appropriate
destination
· IP address needs to be resolved to physical address at each IP network interface
· Example: Ethernet uses 48-bit addresses
o Each Ethernet network interface card (NIC) has globally unique Medium Access Control (MAC) or physical address
o First 24 bits identify NIC manufacturer; second 24 bits are serial number
o 00:90:27:96:68:07 12 hex numbers
Internet Protocol
· It provides best effort, connectionless packet delivery, packets may be lost, out of order, or even duplicated, so it is the responsibility of higher layer protocols to deal with these, if necessary.
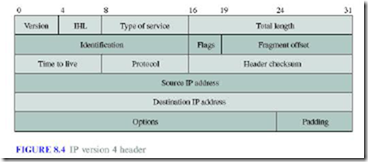
· The header is of fixed-length component of 20 bytes plus variable-length consisting of options that can be up to 40 bytes.
Version: This field identifies the current IP version and it is 4.
Internet header length (IHL): It specifies the length of the header in 32-bit words. If no options are used, IHL will have value of 5.
Type of service (TOS): This field specifies the priority of packet based on delay, throughput, reliability and cost. Three bits are used to assign priority levels and four bits are used for specific requirement (i.e. delay, throughput, reliability and cost).
Total length: The total length specifies the number of bytes of the IP packet including header and data, maximum length is 65535 bytes.
Identification, Flags, and Fragment Offset: These fields are used for fragmentation and reassembly.
Time to live (TTL): It specifies the number of hops; the packet is allowed to traverse in the network. Each router along the path to the destination decrements this value by one. If the value reaches zero before the packet reaches the destination, the router
discards the packet and sends an error message back to the source.
Protocol: specifies upper-layer protocol that is to receive IP data at the destination. Examples include TCP (protocol = 6), UDP (protocol = 17), and ICMP (protocol = 1). Header checksum: verifies the integrity of the IP header of the IP packet.
· IP header uses check bits to detect errors in the header
· A checksum is calculated for header contents
·Checksum recalculated at every router, so algorithm selected for ease of implementation in software
Source IP address and destination IP address: contain the addresses of the source and destination hosts.
Options: Variable length field allows packet to request special features such as security level, route to be taken by the packet, and timestamp at each router. Detailed descriptions of these options can be found in [RFC 791].
Padding: This field is used to make the header a multiple of 32-bit words.
IP Header Processing
1. Compute header checksum for correctness and check that fields in header (e.g. version and total length) contain valid values
2. Consult routing table to determine next hop
3. Change fields that require updating (TTL, header checksum)
IP Addressing
· RFC 1166
· Each host on Internet has unique 32 bit IP address
· Each address has two parts: Netid and Hostid
· Netid is unique & administered by
o American Registry for Internet Numbers (ARIN)
o Reseaux IP Europeens (RIPE)
o Asia Pacific Network Information Centre (APNIC)
· The Net ID identifies the network the host is connected to.
· The host ID identifies each individual system connected to network.
· Dotted Decimal Notation is used for representation:
· The IP address of 10000000 10000111 01000100 00000101 is 128.135.68.5 in
dotted-decimal notation
Classful IP Addresses
· The IP address structure is divided into five address classes: Class A, Class B, Class C, Class D and Class E
· The class is identified by the Most Significant Bit (MSB) of the address as shown below.
· Class A has 7 bits for network IDs and 24 bits for host IDs, allowing up to 126
networks and about 16 million hosts per network.
· Class B has 14 bits for network IDs and 16 bits for host IDs, allowing about 16,000 networks and about 64,000 hosts per network.
· Class C has 21 bits for network IDs and 8 bits for host IDs, allowing about 2 million
networks and 254 hosts per network.
· Class D addresses is used for multicast services that allow host to send information to a group of hosts simultaneously.
· Class E addresses are reserved for experiments.
Subnet Addressing
· Subnet addressing was introduced in the mid 1980s when most large organizations are moving their computing platforms from mainframes to networks of workstations.
· Subnetting adds another level of hierarchical level called “Subnet”.
· Inside the organization the network administrator can choose any combination of lengths for subnet and host ID fields.
· Example: - consider an organization that has been assigned a class B IP address with a network ID of 150.100. Suppose the organization has many LANS, each consisting of not more than 100 hosts. Then seven bits are sufficient to uniquely identify each host in a subnetwork. The other nine bits can be used to identify the subnetworks
within organization
· To find the subnet number, the router needs to store an additional quantity called subnet mask, which consists of binary 1s for every bit position of the address except
the host ID field where binary 0s are used.
· For the IP address 150.100.12.176, the subnet mask is
11111111 11111111 11111111 10000000, which corresponds to 255.255.255.128.
· The router can determine the subnet number by performing a binary AND between subnet mask and the IP address.
The IP address is 10010110 01100100 00001100 10110000 i.e. 150.100.12.176
AND with subnet mask 11111111 11111111 11111111 10000000 i.e. 255.255.255.128
to get subnet number 10010110 01100100 00001100 10000000 i.e.150.100.12.128
and which is also called as First Address and is used to identify the subnetwork inside the organization.
· The IP address 150.100.12.255 is used to broadcast packets inside the subnetwork.
Thus the host connected to subnetwork must have IP address in the range 150.100.12.129 to 150.100.12.254.
Subnetting tips
binary as l l l l l l l l .l lll l l l l.l l l l l l l l .lll00000. Looking at the last octet (because you use this octet for subnetting on a class C address), you 've got three "on"bits, or 1's. So, the formula to figure out how many subnets that this mask will produce is 2n-2,where
n is the number of ..on"bits_ 23-2 = 6 subnets_ Ifyou have memorized your subnet mask
tables from our memorization lists, you'll know this is true and won't have to go through
this procedure.
Let 's try another one.
Let 's say you are going to use the subnet mask 255.255.255.224 with a class B address. Think of the subnet mask in binary as 11111111.11111111.11111111.11100000. Looking at the last two octets (because you use these two octets for subnetting on a class B address), you've got eleven '"on" bits , or 1's. So, the formula to figure out how many
subnets that this mask will produce is 2n-2, where n is the number of '"on" bits. 2ll -2 = 2046 subnets. Ifyou have memorized your subnet mask tables in our memorization lists, you'11know this is true and won't have to go through this procedure .
2.) How many hosts per subnet:
Let 's say you are using the subnet mask 255.255.255.224 with a class C address and you want to figure out how many hosts are available for each subnet. Instead oflooking at the
··on"bits when trying to find the number of subnets, you will be looking at the ..off 'bits orO's. So, once again think of your subnet mask as 1111111L 1111111L 1111111L 11100000_ You '11 see thatthere are five "off ' bits_ So, the formula to figure out how many hosts per subnet that this mask will produce is 2Y-2, wherey is the number of ..ofC bits . 25-2 = 30 hosts per subnet .lf you have memorized your subnet mask tables from our memorization lists, you'11 know this is true and won't have to go through this procedure .
Let 's try another one:
Let's say you are using the subnet mask 255.255.255.0 with a class B address and you want to figure out ho\v many hosts aie available for each subnet . Instead oflooking at the
··an"bits when trying to find the number of subnets, you will be looking at the ··off 'bits or O 's. So, think of your subnet mask as lllll111.lllllll1.11111111.00000000 .You 'll see that there are eight ..off' bits. So, the formula to figure out how many hosts per
subnet that this mask will produce is 2Y-2, where y is the number of '.off 'bits_ 28-2 = 254
hosts per subnet_ If you have memorized yotrr subnet mask tables from our memorization
lists, you'll know this is true and won't have to go through this procedure .
3., 4. and 5.) We can answer all of these at the same time using thefollowing procedure. What are the valid subnets that y ou can obtainfrom the given subnet mask, what is the broadcast address of each subne and what are the valid hosts in each of the subnets.
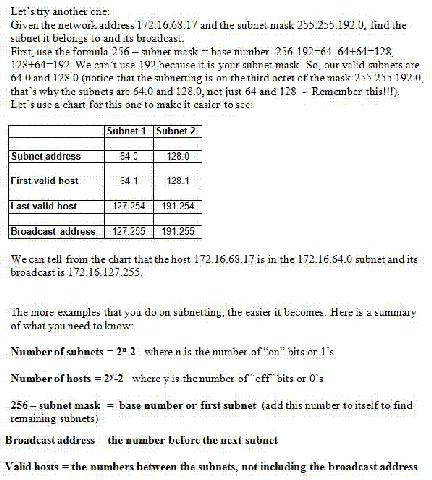
Let 's say that you need to subnet the network address 199.42.78.0 using the subnet mask 255.255.255.224.
First, to figure out the valid subnets, use the formula: 256 -subnet mask= base number. So, your base number is 256- 224 = 32. Nowjust keep adding 32 to itself to get the valid subnets. 32, 32+32=64, 64+32=96 , 96+32=128, 128+32=160, 160+32=192. You can't use 192+32=224 because 224 is your subnet mask. So,your valid subnets are 32, 64, 96,
128, 160, and 192. Let's start making a table to easily see what is happening:
Next, to figure out \vhat the broadcast addresses are for each subnet, just use the number before the next subnet. So, for the subnet address 32, the number before the next subnet 64 is 63. This is the broadcast address for subnet 32. For the subnet address 64, the nwnber before the next subnet 96 is 95. This is the broadcast address for subnet 64.Do this for each subnet .Remember , just use the number before the next subnet . Let's fill in our table to see what we have so far:
Finally. figuring out the valid hosts is easy. Just fill in the numbers bet wee.n the subnet address and the broadcast address .Let 's fill in the rest of the table:
Now that you know ho\v to create the whole table to find all the subnets .the broadcast addresses .and the valid hosts, let's find out how to quickly figure out answers to what you need without doing the whole table.Let's say you receive the following question on the exam :
Using the subnet mask 255.255.255.224, '\vhat is the subnet that the host 199.42.78.133 belongs to and the broadcast for this address?
All you have to do is use your formula 256 - subnet mask =base number. 256-224=32,
which is your frrst subnet.Nowjust add the 32 to itself until you reach the subnet that contains the host 133. 32+32=64 , 64+32=96, 96+32=128, 128+32=160. vVe can stop here
because 133 is between 128 and 160. So, weknow that the address 199.42.78.133
belongs within the 199o42.78.128 subnet and the broadcast is one less than the next subnet of 160, which is 159. So, the broadcast address :is 199.42.78.159.
Example 2
6. This is thefinal question that you saw at th beginning of this document.lfyou are given a particular network and you need x subnets andy hosts, which subnet mask should you use?
The easiest way to do these types of questions is to memorize the subnet mask tables in
our memorization lists.The other way is to use the formulas:
Number of suboets = 211-2 where n is the number of"on"bits or l 's
)lumber of hosts= 2L2 where y is the number of ..off'bits orO's Let's say you receive the follO\ving question on the exam:
You are given the network 130.175.0.0. You want at ]east 70 subnets and 500 hosts per subnet. What subnet mask should you use?
If you memorized our subnet mask tables, you could easily see that you would have to use subnet mask 255.255.254.0 to satisfy these conditions_ If you don'tmemorize the lists, here is one way you could do it:
This is a class B address, so you have 16 bits that can be used for subnetting (the 0.0 in thesubnetmask can be written 00000000.00000000, which is 16 bits).Using your formulas above, you will want to come as close as you can to 70 subnets and 500 hosts . If we start by trying to fmd the amount of subnets (using "on'' bits or 1's), we knov-;r that 26- 2=62 (11111100.00000000) isn't enough subnets so let's use 27-2= 126 (11111110.00000000). This is enough butleCs make sure it ,-..,ill give us enough hosts.
Since we used 27-2=126 (11111110.00000000) for the subnets, we 'vould use the ..off' bits to find the hosts. Since we have 7 "on" bits, this means we have 9 ..off' bits.. So, 29-2=5 l 0, which just gives us enough hosts . This means that 11111110.00000000 would work for the subnet mask. Knowing what we do about binary, let 's add up the "on" bits or l 's: 128+64+32+16+8+4+2=254. So, thesubnet mask would be 255.255.254.0_ You could also figure out this problem finding the hosts first instead of the subnets first.
IP Routing
- IP layer in end-system hosts and in the router work together to route packets from source to destination.
- IP layer in each host and router maintains a routing table, which is used to route the packets based on IP address.
- If a destination host is directly connected to the originating host by a link or by a LAN, then the packet is sent directly to destination host using appropriate network interface, otherwise, the routing table specifies that the packet is to send to default gateway.
- When a router receives an IP packet from one of the network interfaces, then router examines its routing table to see whether the packet is destined to itself or not, if so, delivers to router’s own address, then the router determines the next–hop router and associated network interface, and then forwards the packet.
- Each row in routing table must provide information like: destination IP address, IP address of next-hop router, several flag fields, outgoing network interface, and other information such as subnet mask, physical address.
- H flag indicates whether the route in the given row is to a host (H=1) or to a network.
- G flag indicates whether the route in the given row is to a router (gateway, G=1) or to a directly connected destination (G=0).
- Each time a packet is to be routed, the routing table is searched in the following order.
- First, the destination column is searched to see whether table contains an entry for complete destination IP address.
- If so, then IP packet is forwarded according to next-hop entry and G flag.
- Second, if the table does not contain complete destination IP address, then routing table is searched for the destination network ID.v If an entry found, the IP packet is forwarded according to next-hop entry and G flag.
- Third, if table does not contain destination network ID, the table is searched for default router entry, and if one is available, the packet is forwarded there.
- Finally if none of the above searches are successful, the packet is declared undeliverable and an ICMP “host unreachable error” packet is sent back to originating host.
CIDR
- CIDR stands for Classless Inter-Domain Routing.
- CIDR (Classless Inter-Domain Routing) was introduced in 1993 (RCF 1517) replacing the previous generation of IP address syntax - classful networks. CIDR allowed for more efficient use of IPv4 address space and prefix aggregation, known as route summarization or supernetting.
- CIDR introduction allowed for:
- More efficient use of IPv4 address space
- Prefix aggregation, which reduced the size of routing tables
- CIDR allows routers to group routes together to reduce the bulk of routing information carried by the core routers. With CIDR, several IP networks appear to networks outside the group as a single, larger entity. With CIDR, IP addresses and their subnet masks are written as four octets, separated by periods, followed by a forward slash and a two-digit number that represents the subnet mask
- CIDR was developed in the 1990s as a standard scheme for routing network traffic across the Internet.
- Before CIDR technology was developed, Internet routers managed network traffic based on the class of IP addresses. In this system, the value of an IP address determines its subnetwork for the purposes of routing.
- CIDR is an alternative to traditional IP subnetting that organizes IP addresses into subnetworks independent of the value of the addresses themselves. CIDR is also known as supernetting as it effectively allows multiple subnets to be grouped together for network routing.
CIDR Notation: - CIDR specifies an IP address range using a combination of an IP address and its associated network mask. CIDR notation uses the following format -
xxx.xxx.xxx.xxx/n
where n is the number of (leftmost) '1' bits in the mask. For example,
192.168.12.0/23 applies the network mask 255.255.254.0 to the 192.168 network, starting at 192.168.12.0. This notation represents the address range 192.168.12.0 -
192.168.13.255. Compared to traditional class-based networking, 192.168.12.0/23 represents an aggregation of the two Class C subnets 192.168.12.0 and 192.168.13.0 each having a subnet mask of 255.255.255.0. In other words,
192.168.12.0/23 = 192.168.12.0/24 + 192.168.13.0/24
Additionally, CIDR supports Internet address allocation and message routing independent of the traditional class of a given IP address range. For example,
10.4.12.0/22 represents the address range 10.4.12.0 - 10.4.15.255 (network mask 255.255.252.0). This allocates the equivalent of four Class C networks within the much larger Class A space.
You will sometimes see CIDR notation used even for non-CIDR networks. In non-CIDR IP subnetting, however, the value of n is restricted to either 8 (Class A), 16 (Class B) or 24 (Class C). Examples:
· 10.0.0.0/8
· 172.16.0.0/16
· 192.168.3.0/24
CIDR aggregation requires the network segments involved to be contiguous (numerically adjacent) in the address space. CIDR cannot, for example, aggregate 192.168.12.0 and 192.168.15.0 into a single route unless the intermediate .13 and .14 address ranges are included (i.e., the 192.168.12/22 network).
With CIDR, address classes (Class A, B, and C) became meaningless. The network address was no longer determined by the value of the first octet, but assigned prefix length (subnet mask) address space. The number of hosts on a network, could now be assigned a specific prefix depending upon the number of hosts needed for that network.
ARP (Address Resolution Protocol)
- vThe address resolution protocol (ARP) is a protocol used by the Internet Protocol (IP) specifically IPv4, to map IP network addresses to the hardware addresses used by a data link protocol.
- The protocol operates below the network layer as a part of the interface between the OSI network and OSI link layer. It is used when IPv4 is used over Ethernet.
- It is also used for IP over other LAN technologies, such as Token Ring, FDDI, or IEEE 802.11, and for IP over ATM.
- ARP is a Link Layer protocol because it only operates on the local area network or point-to-point link that a host is connected to.
- The hardware address is also known as the Medium Access Control (MAC) address, in reference to the standards which define Ethernet.
- The Ethernet address is a link layer address and is dependent on the interface card which is used.
- IP operates at the network layer and is not concerned with the link addresses of individual nodes which are to be used. The ARP is therefore used to translate IP addresses into MAC address.
· In the below figure suppose host H1 wants to send an IP packet to H3, but does not know the MAC address of H3. H1 first broadcast an ARP request packet asking the destination host, which is identified by H3’s IP address, to reply. All hosts in the network receive the packet, but only the intended host, which is H3, responds to H1.
· The ARP response packet contains H3’s MAC address and IP addresses.
· H1 caches H3’s MAC address in its ARP table so that H1 can simply look up H3’s MAC address in the table for future use.
- The ARP client and server processes operate on all computers using IP over Ethernet.
The processes are normally implemented as part of the software driver that drives the network interface card.
RARP (Reverse Address Resolution Protocol)
- v RARP is a link layer networking protocol, used to resolve an IP address from a given hardware address (such as an Ethernet address).
- v RARP requires one or more server hosts to maintain a database of mappings from Link Layer address to protocol address.
- v To obtain its IP address, the host broadcasts an RARP request packet containing its MAC address on the network.
- v All hosts in the network receive the packet, but only the server replies to the host by sending an RARP response containing the host’s MAC and IP address.
IP fragmentation and Reassembly
- The Internet Protocol allows IP fragmentation so that datagrams can be fragmented into pieces small enough to pass over a link with a smaller MTU than the original datagram size.
- The Identification field, and Fragment offset field along with Don't Fragment and More Fragment Flags are used for Fragmentation and Reassembly of IP datagrams.
- In a case where a router in the network receives a PDU larger than the next hop's MTU, it has two options. Drop the PDU and send an ICMP message which says "Packet too Big", or to Fragment the IP packet and send over the link with a smaller MTU.
- If a receiving host receives an IP packet which is fragmented, it has to reassemble the IP packet and hand it over to the higher layer.
- Reassembly is intended to happen in the receiving host but in practice it may be done by an intermediate router, for example network address translation requires re- calculating checksums across entire packets, and so routers supporting this will often recombine packets as part of the process.
- The details of the fragmentation mechanism, as well as the overall architectural approach to fragmentation, are different in IPv4 and IPv6.
- In IPv4, routers do the fragmentation, whereas in IPv6, routers do not fragment, but drop the packets that are larger than the MTU size. Though the header formats are different for IPv4 and IPv6, similar fields are used for fragmentation, so the algorithm can be reused for fragmentation and reassembly.
- IP fragmentation can cause excessive retransmissions when fragments encounter packet loss and reliable protocols such as TCP must retransmit all of the fragments in order to recover from the loss of a single fragment.
- Thus senders typically use two approaches to decide the size of IP datagrams to send over the network.
- The first is for the sending host to send an IP datagram of size equal to the MTU of the first hop of the source destination pair.
- The second is to run the "Path MTU discovery" algorithm, to determine the path MTU between two IP hosts, so that IP fragmentation can be avoided.
- The flag field has three bits, one unused bit, one “don’t fragment”(DF) bit, and one “more fragment”(MF) bit.
- If DF bit is set to 1, it forces the router not to fragment the packet. If the packet length is greater than MTU, the router will discard the packet and send an error message to the source host.
- The MF bit tells the destination host whether or not more fragments follow. If there are more, the MF bit is set to 1; otherwise, it is set to 0.
- Fragment offset field identifies the location of a fragment in a packet.
Deficiencies of IP
· Lack of error control, flow control and congestion control
· Lack of assistance mechanisms
What happens if something goes wrong?
· If a router must discard a datagram because it can not find a router to the final destination
· The time-to-leave field has a zero value
· If the final destination host must discard all fragments of a datagram because it has not received all fragments within a pre-determined time limit
IP has no built in mechanisms to notify the original hosts, in erroneous situations
IP also lacks a mechanism for host and management queries
• A host wants to know whether a router or another host is active
• Sometimes network manager needs information from another host or router
Internet Control Message Protocol [ICMP] is companion to IP, designed to compensate these deficiencies
· ICMP is a network layer protocol
· Its messages are encapsulated inside IP datagrams before going to lower layer
· Ping and Traceroute uses ICMP messages,
ICMP Messages
1) Error Reporting Messages
2) Query Messages
1) Error Reporting
· Destination unreachable
· Source quench
· Time exceeded
· Parameters problems
· Redirection
ICMP messages [Error reporting]
1. Destination unreachable
When the subnet or a router can not locate the destination
Or
When a packet with DF bit, can not be delivered because a ‘small-packet’ network stands in the way
2. Time exceeded
When a packet is dropped because its counter has reached zero. This event is a symptom that packets are looping enormous congestion or the time values are being set
too low.
3. Parameter problem
Indicates that an illegal value has been detected in the header field
Indicates a bug in the sending host’s IP software Or Possibly in the software of a router transited.
4. Source quench
To throttle hosts that send too many packets, When a host receives this message, it slows down sending packets
5. Redirect
Is used when a router notices that a packet seems to be routed wrong
It is used by the router to tell the sending host about the probable error.
2) Query Messages
· Echo request and reply
· Time-stamp request and reply
· Address mask request and reply
1. ECHO & ECHO Reply
To see if a given destination is reachable and alive, upon receipt of ECHO message, the destination is expected to send an ECHO REPLY message back.
2. Time stamp & Time stamp reply
Similar to ECHO queries, except that the arrival time of the message and departure time of the reply are recorded in the reply.
This facility is used to measure network performance.
Echo request: type=8; Echo reply: type=0
– Destination replies with echo reply by copying data in request onto reply message
• Sequence number to match reply to request
• ID to distinguish between different sessions using echo services
• Used in PING
ICMP functions
1) Announce network errors: Such as host or Entire portion of the network being unreachable, due to some type of failure. A TCP or UDP packet directed at a port number with no receiver attached is also reported via ICMP.
2) Announce network congestion: When a router begins buffering too many
packets, due to an inability to transmit them as fast as they are being received, it will generate ICMP Source Quench messages. Directed at the sender, these messages should cause the rate of packet transmission to be slowed.
3) Assist Troubleshooting: ICMP supports an Echo function, which just sends a packet on a round--trip between two hosts. Ping, a common network management tool, is based on this feature. Ping will transmit a series of packets, measuring average round—trip times and computing loss percentages.
4) Announce Timeouts: If an IP packet's TTL field drops to zero, the router discarding the packet will often generate an ICMP packet announcing this fact.
















Comments
Post a Comment