QoS & Resource Allocation, VPN, MPLS, Overlay Networks part2
Virtual private network
· A virtual private network (VPN) is a network that uses a public telecommunication infrastructure, such as the Internet, to provide remote offices or individual users with secure access to their organization's network.
· A virtual private network can be contrasted with an expensive system of owned or leased lines that can only be used by one organization.
· The goal of a VPN is to provide the organization with the same capabilities, but at a much lower cost.
· A VPN works by using the shared public infrastructure while maintaining privacy through security procedures and tunneling protocols such as the Layer Two Tunneling Protocol (L2TP).
· In effect, the protocols, by encrypting data at the sending end and decrypting it at the receiving end, send the data through a "tunnel" that cannot be "entered" by data that is not properly encrypted.
· An additional level of security involves encrypting not only the data, but also the originating and receiving network addresses.
· VPNs provides privacy by using tunneling protocols and security procedures
VPN provides the following capabilities
o Extended geographical communication
o Reduced operational cost
o Enhanced organizational management
o Enhanced network management
There are two types of VPNs
o Remote Access VPN
o Site-to-Site VPN
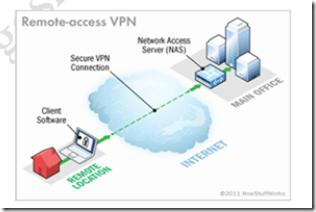
1. Remote Access VPN
· Remote access tunneling is a user to LAN connection.
· Organization users are connected to a private network from various remote locations by using remote access VPN.
· Remote access VPNs use encrypted connections between the organizations private network and remote users through a third party that provider service.
· Tunneling uses mainly the point to point protocol in remote access VPN.
· To communicate over internet PPP helps by carrying other internet protocols as IPsec, L2F, PPTP and L2TP.
Layer 2 Forwarding (L2F) Protocol: it uses the authentication scheme supported by PPP.
Point to Point Tunneling Protocol (PPTP): It supports 40 bit and 128 bit encryption format and uses the authentication method supported by PPP.
Layer 2 Tunneling Protocol (L2TP): It combines the features of both PPTP and L2F.
2. Site to Site VPN
Site to site tunneling is used to connect multiple fixed sites of an organization over a public network.
It can be classified as either intranet or extranet
1. Internet : it is used to connect various remote site LANS of an organization into a private network
2. Extranet: it allows two organizations to work in a shared environment through a tunnel built to connect them.
Three types of VPNs are shown in below figure.
The office 1 main campus and branch campus are connected through the intranet VPN. The office 1 main campus also connected to office 2 through the extranet VPN.
The office 1 main campus can also access their corporation through a remote-access VPN. The main benefit of a VPN is scalability with a reasonable cost.
Both Generic Routing Encapsulation (GRE) and IPsec are encapsulating protocols used in site-to-site VPN
Figure. Three types of VPN: Remote VPN,Site to Site VPN(Intranet and Extranet VPN)
Tunneling and Point to Point Protocol (PPP)
A connection that forms a virtual network is called a tunnel. Tunneling is a process of encapsulating packets and sending them over the public network.
Point-to-Point connections are used to create tunnels through the internet.
When employees of a company are located outside of main office over different cities they used to create tunnels.
Tunneling connections need to be secure since they run over the internet.
Tunneling process requires internet protocols, carrier protocols and encapsulating protocols.
1. Carrier protocols, through which information travels over the public network
2. Encapsulating protocols, though which data is wrapped, encapsulated and secured.
· The figure below shows two LANs of two offices connected through the internet using tunnels.
· Suppose office 1 and office 2 use their own networking protocols denoted by X.
· X-type packet cannot run over the internet directly.
· The IP Gateway R1 on office 1 listens for X-type packets and encapsulates them in transport layer UDP datagrams to transmit them to IP Gateway R2.
· When R2 receives these packets it decapsulates and sends them to office 2, thus two offices communicate each other.
Security in VPNs
· Companies can create their own VPNs to remote employees and distant offices for communication.
· When they establish VPN connection they need to think about security.
· Using firewalls, encryption system, IPsec features and authentication server they can provide a well protected virtual private network.
1. firewall: a firewall acts as an effective barrier between private network and the internet.
2. Encryption System: these systems are used to hide the original information by giving some other representation to it.
3. Authentication Server: performs authentication and authorization and accounting for more secure access in a remote-access environment.
Multiprotocol Label Switching
· Multiprotocol Label Switching (MPLS) refers to a mechanism which directs and transfers data between Wide Area Networks (WANs) nodes with high performance, regardless of the content of the data.
· MPLS makes it easy to create "virtual links" between nodes on the network, regardless of the protocol of their encapsulated data.
· It is a highly scalable, data-carrying mechanism.
· In an MPLS network, data packets are assigned labels.
· Packet-forwarding decisions are made solely on the contents of this label, without the need to examine the packet itself.
· This allows one to create end-to-end circuits across any type of transport medium, using any protocol.
· The primary benefit is to eliminate dependence on a particular Data Link Layer technology, such as ATM, frame relay, SONET or Ethernet, and eliminate the need for multiple Layer 2 networks to satisfy different types of traffic.
· MPLS belongs to the family of packet-switched networks.
· MPLS operates at an OSI Model layer that is generally considered to lie between traditional definitions of Layer 2 (Data Link Layer) and Layer 3 (Network Layer), and thus is often referred to as a "Layer 2.5" protocol.
· It was designed to provide a unified data-carrying service for both circuit-based clients and packet-switching clients which provide a datagram service model.
· It can be used to carry many different kinds of traffic, including IP packets, as well as native ATM, SONET, and Ethernet frames.
· MPLS attempts to preserve the traffic engineering and out-of-band control that made frame relay and ATM attractive for deploying large-scale networks.
MPLS Operation
MPLS works by prefixing packets with an MPLS header, containing one or more 'labels'. This is called a label stack. Each label stack entry contains four fields:
• A 20-bit label value.
• A 3-bit Traffic Class field for QoS (Quality of Service) priority (experimental) and ECN (Explicit Congestion Notification).
• A 1-bit bottom of stack flag. If this is set, it signifies that the current label is the last in the stack.
• An 8-bit TTL (time to live) field.
Figure : MPLS header encapsulation for an IP packet
· These MPLS-labeled packets are switched after a Label Lookup/Switch instead of a lookup into the IP table.
· As mentioned above, when MPLS was conceived, Label Lookup and Label Switching were faster than a RIB lookup because they could take place directly within the switched fabric and not the CPU.
· The entry and exit points of an MPLS network are called Label Edge Routers (LER), which, respectively, push an MPLS label onto an incoming packet and pop it off the outgoing packet.
· Routers that perform routing based only on the label are called Label Switch Routers (LSR).
Routing in MPLS Domain
1. Ingress LSR
2. Core LSR
3. Egress LSR
1) Ingress LSR: This performs initial packet processing and applies the first label to create a new label.
2) Core LSR: This swaps the incoming label with the corresponding next hop label given by a forwarding table.
3) Egress LSR: This pops the label from the packet.
When an IP packet enters into an MPLS domain an ingress LSR processes its information and matches it to a Forward Equivalence Class (FEC).
The QoS parameters also define which queueing and discarding policy are to be used. Two protocols are used to exchange information among routers, and they are,
i) Intradomain Routing Protocol
ii) Label Distribution Protocol
Intradomain Routing Protocol (OSPF): This is used to exchange routing information
Label Distribution Protocol: This assigns labels to each packet.
Tunneling and Use of FEC
Any traffic in MPLS operation can be grouped into FECs (Forward Equivalence Classes). FEC means a group of IP packets are forwarded in the same manner i.e., over the same path or with the same forwarding procedure.
A packet can be mapped to FEC based on the criteria given below,
o Source/destination IP address or IP network address,
o TCP/UDP connection
o Class of service
o Applications
Route selection can be done either hop-by-hop or explicit routing.
1. Hop-by-hop: with this routing, each LSR can choose the next hop for each FEC. But this routing does not support traffic engineering.
2. Explicit Routing: This supports traffic engineering and can also provide all the benefits of traffic engineering. In this routing a single LSR determines the LSP for a given FEC.
Constraint based routing allows FECs to separate the traffic into different levels of QoS to support a variety of services such as security based VPN and latency based voice traffic.
Traffic engineering
In MPLS, traffic engineering is an automated scheme that controls signaling and link bandwidth assignment to improve the quality of network management.
Traffic engineering can be either traffic oriented or resource oriented.
1) Traffic oriented: which include the optimization of traffic performance parameters such as minimization packet delay, packet loss and quick fault recovery when a node or link fails.
2) Resource Oriented: This includes the optimization of network resource utilization.
MPLS based VPNs
· MPLS based VPN is easier to manage VPN sites and VPN membership using multiprotocol based Border Gateway Protocol (BGP).
· MPLS network domain acts as a backbone network between VPN users.
· A core router acts as a providing routers and edge routers acts as costumer edge routers.
· These costumer edge routers distribute VPN information through MPLS_BGP to other providing routers.
· LSRs that function as ingress and/or egress routers to the VPN are often called PE (Provider Edge) routers.
· Devices that function only as transit routers are similarly called P (Provider) routers.
· The job of a Provider router is significantly easier than that of a PE router, so they can be less complex and may be more dependable because of this.
Overlay Networks
· To protect the existing network from the internet use by the new protocols during testing phase in public network
· Overlay network creates a virtual topology on top of existing physical topology.
· The above figure shows an overlay network over a wide-area-network
· In an overlay network logical links are used to connect all nodes.
· Here R3, R5, R7 and R2 routers are used to form the overlay network designing with overlay logical links as the interconnection links.
· Logical link is a path used to connect two nodes in an overlay network
· Peer-to-peer network is an example of an overlay network, which runs on top of internet
· Overlay network improve internet routing by allowing the routing of messages to the destination without knowing its IP address.
· Overlay networks are self organized networks. Thus if a node fails in the overlay network algorithm should provide solutions to recreate an appropriate network structure.









Comments
Post a Comment