Network management:Key Generation
Key Generation
1) Generate two large prime numbers, p and q
To make the example easy to follow I am going to use small numbers, but this is not secure. To find random primes, we start at a random number and go up ascending odd numbers until we find a prime. Lets have:
p = 7
q = 19
2) Let n = pq
n = 7 * 19
= 133
3) Let m = (p - 1)(q - 1)
m = (7 - 1)(19 - 1)
= 6 * 18
= 108
4) Choose a small number, e coprime to m
e coprime to m, means that the largest number that can exactly divide both e and m (their greatest common divisor, or GCD) is 1. Euclid's algorithm is used to find the GCD of two numbers, but the details are omitted here.
e = 2 => GCD(e, 108) = 2 (no)
e = 3 => GCD(e, 108) = 3 (no)
e = 4 => GCD(e, 108) = 4 (no)
e = 5 => GCD(e, 108) = 1 (yes!)
5) Find d, such that de % m = 1
This is equivalent to finding d which satisfies de = 1 + nm where n is any integer. We can rewrite this as d = (1 + nm) / e. Now we work through values of n until an integer solution for e is found:
n = 0 => d = 1 / 5 (no)
n = 1 => d = 109 / 5 (no)
n = 2 => d = 217 / 5 (no)
n = 3 => d = 325 / 5 = 65 (yes!)
To do this with big numbers, a more sophisticated algorithm called extended Euclid must be used.
Public Key Secret Key
n = 133
e = 5
n = 133
d = 65
Communication
Encryption
The message must be a number less than the smaller of p and q. However, at this point we don't know p or q, so in practice a lower bound on p and q must be published. This can be somewhat below their true value and so isn't a major security concern. For this example, lets use the message "6".
C = Pe % n
= 65 % 133
= 7776 % 133
= 62
Decryption
This works very much like encryption, but involves a larger exponentiation, which is broken down into several steps.
We now repeat the sequence of operations that reduced 6265 to 12032 to reduce the exponent down to 1.
A very simple example of RSA encryption
This is actually the smallest possible value for the modulus n for which the RSA algorithm works.
Now say we want to encrypt the message m = 7, c = me mod n = 73 mod 33 = 343 mod 33 = 13. Hence the ciphertext c = 13.
To check decryption we compute m' = cd mod n = 137 mod 33 = 7.
Note that we don't have to calculate the full value of 13 to the power 7 here. We can make use of the fact that
a = bc mod n = (b mod n).(c mod n) mod n
so we can break down a potentially large number into its components and combine the results of easier, smaller calculations to calculate the final value.
One way of calculating m' is as follows:-
m' = 137 mod 33 = 13(3+3+1) mod 33 = 133.133.13 mod 33
= (133 mod 33).(133 mod 33).(13 mod 33) mod 33
= (2197 mod 33).(2197 mod 33).(13 mod 33) mod 33
= 19.19.13 mod 33 = 4693 mod 33
= 7.
APPLICATIONS:- Domain Name Service (DNS)
.DNS is a host name to IP address translation service
. DNS is a distributed database implemented in a hierarchy of name servers, an application level protocol for message exchange between clients and servers
. A lookup mechanism for translating objects into other objects
. A globally distributed, loosely coherent, scalable, reliable, dynamic database
.Comprised of three components
. A “name space”
. Servers making that name space available
. Resolvers (clients) which query the servers about the name space
. It is easier to remember a host name than it is to remember an IP address.
.A name has more meaning to a user than a 4 byte number.
. Applications such as FTP, HTTP, email, etc., all require the user to input a destination.
.The user generally enters a host name.
.The application takes the host name supplied by the user and forwards it to DNS for translation to an IP address.
.DNS works by exchanging messages between client and server machines.
. A client application will pass the destination host name to the DNS process to get the IP address.
.The application then sits and waits for the response to return.
How DNS Works
. Client wants IP for www.amazon.com; 1st approx:
. client queries a root server to find com DNS server
. client queries com DNS server to get amazon.com DNS server
. client queries amazon.com DNS server to get IP address for www.amazon.com
Domain Name Space
To have a hierarchical name space, a domain name space was designed. In this design the
names are defined in an inverted-tree structure with the root at the top. The tree can have only 128 levels: level 0 (root) to level 127.
Zones and Domains
.Zones are “administrative spaces”
. Zone administrators are responsible for portion of a domain’s name space
. Authority is delegated from a parent and to a child
Generic Domains
Telnet
· TELNET is a general protocol, meant to support logging in from almost any type of terminal to almost any type of computer.
· It allows a user at one site to establish a TCP connection to a login server or terminal server at another site.
· A TELNET server generally listens on TCP Port 23.
How it works
· A user is logged in to the local system, and invokes a TELNET program (the TELNET client) by typing
· telnet xxx.xxx.xxx
where xxx.xxx.xxx is either a host name or an IP address.
· The TELNET client is started on the local machine (if it isn't already running). That client establishes a TCP connection with the TELNET server on the destination system.
· Once the connection has been established, the client program accepts keystrokes from the user and relays them, generally one character at a time, to the TELNET server.
· The server on the destination machine accepts the characters sent to it by the client, and passes them to a terminal server.
· A "terminal server" is just some facility provided by the operating system for entering keystrokes from a user's keyboard.
o The terminal server treats the remote user as it would any other user logged in to the system, including relaying commands to other applications.
o The terminal server passes outputs back to the TELNET server, which relays them to the client, which displays them on the user's screen.
· In general, a TELNET server is implemented as a master server with some number of slave servers. The master server listens for service requests from clients. When it hears one, it spawns a slave server to handle that specific request, while the master goes back to listening for more requests.
· The only thing that makes TELNET hard to implement is the heterogeneity of the terminals and operating systems that must be supported. Not all of them use the same control characters for the same purposes.
· To accomodate this heterogeneity, TELNET defines a Network Virtual Terminal (NVT).
Any user TELNETting in to a remote site is deemed to be on an NVT, regardless of the actual terminal type being used.
· It is the responsibility of the client program to translate user keystrokes from the actual terminal type into NVT format, and of the server program to translate NVT characters into the format needed by the destination host. For data sent back from the destination host, the translation is the reverse.
· NVT format defines all characters to be 8 bits (one byte) long. At startup, 7 bit US ASCII is used for data; bytes with the high order bit = 1 are command sequences.
· The 128 7-bit long US ASCII characters are divided into 95 printable characters and 33 control codes. NVT maps the 95 printable characters into their defined values - decimal 65 = "A", decimal 97 = "a", etc.
· The 33 control codes are defined for NVT as:
Secure Shell [SSH]
Secure Shell (SSH) Protocol is a protocol for secure network communications designed to be relatively simple and inexpensive to implement. The initial version, SSH1, focused on providing a secure remote logon facility to replace Telnet and other remote logon schemes that provided no security.
SSH also provides a more general client-server capability and can be used to secure such network functions as file transfer and e-mail.
A new version, SSH2, provides a standardized definition of SSH and improves on SSH1 in numerous ways. SSH2 is documented as a proposed standard in RFCs 4250 through.
SSH client and server applications are widely available for most operating systems. It has become the method of choice for remote login and X tunneling and is rapidly becoming one of the most pervasive applications for encryption technology outside of embedded systems. SSH is organized as three protocols that typically run on top of TCP (Figure 1):
· Transport Layer Protocol: Provides server authentication, data confidentiality, and data integrity with forward secrecy (that is, if a key is compromised during one session, the knowledge does not affect the security of earlier sessions); the transport layer may optionally provide compression
· User Authentication Protocol: Authenticates the user to the server
· Connection Protocol: Multiplexes multiple logical communications channels over a single underlying SSH connection
Applications:- SMTP [Simple Mail Transfer Protocol]
SMTP was developed to send e-mail messages across the Internet.
In the OSI model, SMPT is an application layer protocol that utilizes TCP as the transport protocol to transmit mail to a destination mail exchanger, in other words, SMTP is used to transmit mail to a mail server. Mail can be transmitted by a client to the mail exchanger server, or from mail exchanger to mail exchanger.
Mail sent via SMTP is usually sent from one mail exchanger to another, directly. E-mail was never designed to be instantaneous, but that is often how it appears to us.
Mail Exchangers (MX)
Mail Exchangers are the name given to the applications that support the SMTP protocol. Mail Exchangers such as sendmail or Microsoft Exchange should listen for IP datagrams that arrive on the network interface with a TCP port number of 25 and on . This port is one of the 'well known ports' defined in RFC 1700. When a message is received, the mail exchanger should check to see if it is for one of it's users, then move the mail to the user's mailbox.
To identify the mail exchangers for a domain name, DNS zone files for the domain contain an MX resource record identifying the host name and IP address of the mail exchangers.
Simple mail transfer protocol differs from Post Office Protocol version 3 (POP3). POP3 is used by e-mail client applications such as Microsoft Outlook, Mozilla Thunderbird, Eudora and other e-mail applications to retreive mail stored in personal mailboxes at the mail server.
E-Mail Clients
E-mail is a client-server protocol that allows the exchange of messages and attachments in various formats. An e-mail client is a software application which seamlessly handles all the technical communications tasks to connect to and find the e-mail at the server, download the e-mail messages, organizes them and presents them to the user in a usable format. An e-mail client also provides the means to compose new messages, reply to and forward received messages, and to organize the messages for later review.
E-mail clients use POP3 or IMAP instead of SMTP. SMTP is used strictly between mail servers.
POP3 :- Post Office Protocol version 3 (POP3) is a standard mail protocol used to receive emails from a remote server to a local email client. POP3 allows you to download email messages on your local computer and read them even when you are offline.
IMAP:- The Internet Message Access Protocol (IMAP) is a mail protocol used for accessing email on a remote web server from a local client. IMAP and POP3 are the two most commonly used Internet mail protocols for retrieving emails. Both protocols are supported by all modern email clients and web servers.
Main difference between IMAP and POP3:
The POP3 protocol assumes that there is only one client connected to the mailbox. In contrast, the IMAP protocol allows simultaneous access by multiple clients. IMAP is suitable for you if your mailbox is about to be managed by multiple users.
Third scenario in electronic mail
Applications:- File Transfer Protocol [FTP]
.FTP is an Internet (or more properly a TCP/IP) communications protocol to allow you to upload and download files from a machine connected to your local machine via the Internet. FTP is composed of two parts; an FTP client and an FTP server. The FTP client is the software you execute on your local machine to send or receive files. The FTP server is software which executes on a server machine on which the files are to be saved or retrieved. Most (if not all) machines which provide Web serving capability also serve as FTP servers to allow you to upload your web pages. Web pages are usually composed of HTML source files and images (either JPEG or GIF format).
. You should run FTP client software to connect to a FTP server on the Net.
. You must use an account to login.
. Username / password
.Anonymous / email address
. HTTP can be used for downloading file on the Web, but not as efficient as FTP.
. There are two modes of transfer in FTP:
. ascii
. binary.
. ASCII is used only for files saved in ASCII format (this includes Postcript files)
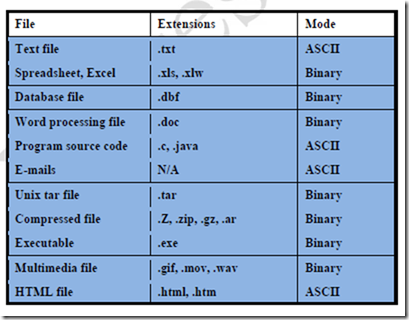
Binary is used for files that are formatted and saved using a wordprocessing software like WordPerfect (.txt), spreadsheets (.xls), images (.jpg, .gif), and many executable programs (.exe) and videos (.avi).
FTP Example
There are many commands that can be used at the ftp prompt and users should refer to the manual page for full descriptions of all ftp interpreter commands.
Listing a Directory. Usually, the first command after making a connection is to list the contents of the directory. At the ftp prompt, type `ls' for a short-format listing or `dir' for a long-format listing.
Changing Directories. The next action you may want to take is to change to a subdirectory, which can be accomplished by typing `cd remote-directory' where `remote-directory' is the desired directory.
Transferring Files. Other important commands are the get and put commands, for example
`get remote-filename local-filename' gets a file named `remote-filename' from the remote machine and stores it as `local-filename' on the local machine. If the file is not just plain text (an executable for example), you may want to change to binary mode by entering the `binary' command before your file tranfer. To transfer multiple files, type `prompt off' and use the `mput' or `mget' commands with a file specification to match files, for example `mget *.c' to get all files with a `.c' extension. To abort a file transfer, use the terminal interrupt key (usually CTRL-C). Once you have ftp'ed files from remote system(s), you can view or edit text file(s) using your editor, run binaries for Sun Sparcstations from the Unix shell, or download file(s) to your home computer.
Exiting. To terminate the ftp connection with the reomte server and exit ftp, type `bye' or
`quit'.
Applications:- World Wide Web [WWW]
. The Internet has much to offer in terms of information on almost any subject matter imaginable and interaction with people and organizations from all over the world. Much of this access and interaction make use of the environment which is popularly known as the World Wide Web (WWW) or web. The WWW is an interlinked network of systems, called web servers, offering multimedia services and information. A user can access these using what is known as web browser software.
. The world wide web is a system of Internet servers that supports hypertext and multimedia to access several Internet protocols on a single interface. The World Wide Web is often abbreviated as the web or www.
. The World Wide Web was developed in 1989 by Tim Berners-Lee of the European Particle Physics Lab (CERN) in Switzerland. The initial purpose of the Web was to use networked hypertext to facilitate communication among its members, who were located in several countries.
Protocols of the Web
.The surface simplicity of the Web comes from the fact that many individual protocols can be contained within a single Web site. internet protocols are sets of rules that allow for intermachine communication on the Internet. These are a few of the protocols you can experience on the Web:
. HTTP (HyperText Transfer Protocol): transmits hyptertext over networks. This is the protocol of the Web.
. E-mail (Simple Mail Transport Protocol or SMTP): distributes e-mail messages and attached files to one or more electronic mailboxes.
. FTP (File Transfer Protocol): transfers files between an FTP server and a computer, for example, to download software.
. VoIP (Voice over Internet Protocol): allows delivery of voice communications over IP networks, for example, phone calls.
Hypertext and links: the motion of the Web
. The operation of the Web relies primarily on hypertext as its means of information retrieval. HyperText is a document containing words that connect to other documents. These words are called links and are selectable by the user.
. A single hypertext document can contain links to many documents. In the context of the Web, words or graphics may serve as links to other documents, images, video, and sound. Links may or may not follow a logical path, as each connection is created by the author of the source document. Overall, the Web contains a complex virtual web of connections among a vast number of documents, images, videos, and sounds.
. Producing hypertext for the Web is accomplished by creating documents with a language called hypertext markup language, or html. With HTML, tags are placed within the text to accomplish document formatting, visual features such as font size, italics and bold, and the creation of hypertext links.
<p> This is a paragraph that shows the underlying HTML code. <strong>This sentence is rendered in bold text</strong>. <em>This sentence is rendered in italic text.</em> </p>
.HTML is an evolving language, with new tags being added as each upgrade of the language is developed and released. Nowadays, design features are often separated from the content of the HTML page and placed into cascading style sheets (css). This practice has several advantages, including the fact that an external style sheet can centrally control the design of multiple pages. The World Wide Web Consortium (W3C), led by Web founder Tim Berners-Lee, coordinates the efforts of standardizing HTML. The W3C now calls the language XHTML and considers it to be an application of the XML language standard.
. Pages on the Web
. The backbone of the World Wide Web are its files, called pages or Web pages,
containing information and links to resources - both text and multimedia - throughout the Internet.
. Web pages can be created by user activity. For example, if you visit a Web search engine and enter keywords on the topic of your choice, a page will be created containing the results of your search.
. Access to Web pages can be accomplished in all sorts of ways, including:
. Entering a Web address into your browser and retrieving a page directly
. Browsing through sites and selecting links to move from one page to another both within and beyond the site
. Doing a search on a search engine to retrieve pages on the topic of your choice (See:
The World of Search Engines)
. Searching through directories containing links to organized collections of Web pages (See: The World of Subject Directories)
. Clicking on links within e-mail messages
.Using apps on social networking sites or your mobile phone to access Web and other online content
. Retrieving updates via RSS feeds and clicking on links within these feeds (See: RSS Basics) Retrieving doucuments on the Web: the URL and Domain Name System
. url stands for uniform resource locator. The URL specifies the Internet address of a file stored on a host computer, or server, connected to the Internet. Web browsers use the URL to retrieve the file from the server. This file is downloaded to the user's computer, or client, and displayed on the monitor connected to the machine. Because of this relationship between clients and servers, the Web is a client-server network.
Programming languages and environments
. The use of programming languages beyond HTML extend the capabilities of the Web. They are used to write software, process Web forms, fetch and display data, and perform all kinds of advanced functions. It is difficult to talk about these languages without getting into too much technical jargon, but here is an attempt. What follows is a brief guide to some of the more common languages in use on the Web today.
. CGI (Common Gateway Interface) refers to a specification by which programs can communicate with a Web server. A CGI program, or script, is any program designed to process data that conforms to the CGI specification. The program can be written in any programming language, including C, Perl, and Visual Basic Script (VBScript). In the early days of the Web, CGI scripts were commonly used to process a form on a Web page. Perl is popular with Google, and is also the language of the Movable Type blog platform.
. Active Server Pages (ASP): Developed by Microsoft, ASP is a programming environment that processes scripts on a Web server. The programming language VBScript is often used for the scripting. Lightweight programs can be written with this language. Active Server Pages end in the file extension .asp. For an example, check out Databases and Indexes at the University at Albany Libraries.
. .NET framework: Also developed by Microsoft, this development framework is a more powerful one than ASP for writing applications for the Web. Programming languages include C+ and VB.Net. ASP.Net is a related environment, producing pages with the file extensions .aspx. The Microsoft site is a good example of a site created with the .NET framework.
. PHP: This is another server-based language. It is frequently the language used to write open source (e.g., nonprofit, community-created) programs found on the Web, including MediaWiki (the software that runs the Wikipedia), and the popular blog software WordPress. While PHP functionality can be installed on Windows servers, it is native to the Linux server environment and commonly used there.
. Java/Java Applets: Java is a programming language similar to C++. Developed by Sun Microsystems, the aim of Java is to create programs that will be platform independent. The Java motto is, "Write once, run anywhere." A perfect Java program should work equally well on a Windows, Apple, Unix, or Linux server, and so on, without any additional programming. This goal has yet to be realized. Java can be used to write applications for both Web and non-Web use.
. Web-based Java applications are usually in the form of Java servlets. These are small Java programs fetched from within a Web page that can be downloaded from a server and run on a Java-compatible Web browser. A Web page that links to a Java servlet has the file extension .jsp.
. JavaScript is a very popular programming language created by Netscape Communications. Small programs written in this language are embedded within a Web page, or fetched externally from within the page, to enhance the page's functionality. Examples of JavaScript include drop-down menus, image displays, and mouse-over interactions. The drop-down menus on the site of the UCLA Library shown below are a good example: when you hover your mouse over the menu item, a set of sub-menus opens up below.
. XML: XML (eXtensible Markup Language) is a mark-up language that enables Web designers to create customized tags to provide functionality not available with HTML
alone. XML is a language of data structure and exchange, and allows developers to separate form from content. With XML, the same content can be formatted for multiple applications. In May 1999, the W3 Consortium announced that HTML 4.0 has been recast as an XML application called XHTML.
. AJAX stands for Asynchronous JavaScript and XML. This langauge is used to create interactive Web applications. Its premise is that it sends data to the browser behind the scenes, so that when it is time to view the information, it is already "there." Google Maps is a well-known example of AJAX. A different kind of example can be found with SurfWax LookAhead, an RSS search tool that retrieves feeds as you type your search.
. SQL (Structured Query Language): This is a language that focuses on extracting data from databases. Programmers write statements called queries that retrieve data from the tables in the database. Some Web sites are created extensively or entirely from data stored in database tables. You can often tell that a SQL query has produced data on a page by the presence of a question mark (?) and a record number in the URL, as the example below illustrates.
. Mashups
. Programs on the Web can be flexible. Sometimes they are combined with each other to form ehanced presentations. These are known as mashups.
. A mashup is a Web application or Web page that combines data from two or more external sources. Mashups give you access in one place to information available in multiple places.



















Comments
Post a Comment