TCP/IP-1 part2
Internet is growing explosively……!!??
· Internet is growing explosively, computer, communication, home appliances and entrainment industries are converging, wireless users are increasing, every telephone,
TV, appliance in the world may become internet node.
Today’s IPv4 will not support this demand!!!!? Severe scarcity of IP
addresses!!!!?
The solution is IPv6, Next generation protocol to sustain the growth of internet
IPv6 Goals
· It support billions of hosts and provide better security (authentication and privacy) than current IP.
· The IP protocol is simplified when compared to IPV4, which makes the router to process the packet at faster rate.
· It permit the old and new protocols to co-exits for years
· IPV6 maintains good features of IPV4; discards or deemphasizes the badness
· IPV6 is not compatible with IPV4, but it is compatible with other auxiliary Internet protocols like:-TCP,UDP,ICMP,IGMP,OSPF,BGP,DNS
The changes made in IPV6 when compared to IPV4 are:-
i) Longer address fields: - The length of address field is extended from 32 bits to 128 bits and this huge address space supports up to 3.4 X 1038.
ii) Simplified Header format: - The header format of IPV6 is simpler than IPV4 because some fields in IPV4 are removed from IPV6, such as checksum, IHL, identification, flags, and fragment offset.
iii) Flexible support for options: - The options in IPV6 appear in optional extension headers.
iv) Security: - IPV6 supports built-in authentication and confidentiality.
v) Large Packets: - IPV6 supports payloads that are longer than 64K bytes the packets that are longer than 64K bytes are called jumbo payloads.
vi) Fragmentation at source only: - Here fragmentation is done at source by finding minimum MTU along the path.
vii) No checksum field: - The checksum field is removed to reduce packet processing time in a router.
IPV6 Header Format

Traffic class: - This field specifies the traffic class or priority of the packet.
Flow label:- This field can be used to identify the QoS requested by the packet.
It provides a special treatment for the packet and needs special handling by the intervening routers
Payload length:- This field identifies the total length of the data excluding the basic header and it is limited to 65,535 bytes because only 16 bits is used in basic header to represent the payload length. To send larger payloads use the options in extension header.
Next header: - This field identifies the type of extension header (optional) header that follows the basic header.[There are up to 6 extension headers]. If this header is the last IP header, this field tells which transport (upper layer) protocol handler to pass the packet in [as in Protocol field in IPV4]
Hop limit:- Same as TTL in IPv4, it contains the number hops the packet has to traverse in the network and it is decremented at each hop.
Source address: - 16 Byte (128 bits) to identify the source of the datagram
Destination address: - 16 Byte (128 bits) to typically to identify the final destination of the datagram
• However, if the source routing is used, this field contains the address of the next router.
Network Addressing
IPV6 addresses are divided into three categories:-
1. Unicast addresses identify a single network interface.
2. Multicast addresses identify a group of network interfaces, typically at different locations. A packet will be sent to all network interfaces in the group.
3. Anycast addresses identify a group of network interfaces. However, a packet will be sent to all network interfaces in the group.
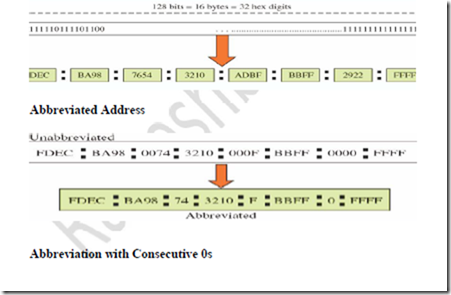
IPV6 uses a compact notation to represent its address i.e a hexadecimal digit for every 4 bits and to separate every 16 bits with a colon.
Example:-
· IPV6 assigns few addresses for special purposes.
· Address 0::0 is called unspecified address and it is never used as a destination address
· Address ::1 is used as loopback address
· IPV4 –compatible addresses are used by IPV6 routers and hosts that are directly connected to an IPV4 network.
· IP –mapped addresses are used to indicate IPV4 routers and hosts that do not support IPV6.
· Provider based Unicast addresses are identified by the prefix 010. It is mainly used by service providers to assign addresses to their subscribers and format is as shown in the diagram.
The first level is identified by the registry ID, which is managed by ARIN (North America), RIPE (Europe), APNIC (Asia Pacific). Next level identifies the Internet Service Provider that is responsible for assigning the subscriber IDs. Finally each subscriber assigns the address according to subnet IDs and interface IDs.
Extension Headers
· Extension Headers support extra functionalities that are not provided by basic header
· IPV6 allows any number of extension headers to be placed between the basic header and payload.
· The extension headers are daisy chained by the next header field, which appears in basic header as well as in each extension header.
· The above figure illustrates the use of next header field.
LARGE PACKET
· IPV6 allows payload size greater than 64K by using extension header
· Payload size greater than 64K is used people who work in supercomputers
· Next header field identifies the type of header immediately following this header
· Value 194 defines jumbo payload option.
· Payload length in basic header must be set to 0.
· Option length field specifies size of jumbo payload in bytes.
· Like IPv4, IPv6 allows source to specify the sequence of routers to be visited by a packet to reach destination.
· This option is defined by routing extension header, and figure is as shown above.
· Header length specifies the length of the routing extension header in units of 64 bits.
· Segment left field identifies the number of route segments remaining before the destination is reached, initially this value will be set to total number of route segments
from source to destination. Each router decrements this value by 1 until the packet reaches destination.
· Each bit in the strict/loose bit mask indicates whether the next destination address must be followed strictly (if the bit is set to 1) or loosely (if the bit is set to 0).
FRAGMENTATION
· IPv6 allows only source host to perform fragmentation.
· If the packet length greater than the MTU of the network, an intermediate router discards the packet and sends an ICMP error message back to source.
· Source can find minimum MTU along the path from source to destination by performing
“path MTU discovery” procedure.
· Advantage of doing fragmentation at source only is that router can process packets faster.
· Disadvantage is that path between source and destination must be static, so that path MTU discovery does not give outdated information.
· Fragment offset, M(more fragment), and identification fields have the same purposes as they have in IPv4 except identification is now extended to 32bits.
Figure: - Fragment Extension Header
What has been left out in IPv6 compared to IPv4?
1. IHL field
• Because IPv6 has a fixed length
2. Protocol field
• The Next Header field takes care of this
3. All fields related to fragmentation
IPv6 takes different approach to fragmentation
4. Checksum field
• Assumed that physical layers are more reliable
• Assumed that data link layer and transport layer will take care of this
• To increase the performance.
Migration or Transition Issues from IPv4 to IPv6
· When islands of IPv6 networks are separated by IPv4 networks, one approach is to build a tunnel across an IPv4 network connecting two IPv6 networks.
· A tunnel is a path created between two nodes so that the tunnel appears as a single link to the user.
· In the below figure IPv6 packets are first forwarded from the source to the tunnel head- end in the IPv6 network. At the tunnel head-end the packets are encapsulated into IPv4 packets. Then IPv4 packets are forwarded in the IPv4 network to the tunnel tail-end where the reverse process (i.e. decapsulation) is performed.
· Finally, IPv6 packets are forwarded from the tunnel tail-end to the destination.
User datagram Protocol (UDP)
UDP is a transport protocol
· UDP provides communication between processes
· UDP uses IP to deliver datagrams to the right host
· Connectionless
· No session is established. Does not provide guaranteed delivery
· No sequence numbers
· No acknowledgements
· No flow control
· No error control
· Reliability is the responsibility of the application. Uses Port numbers as endpoints to communicate
Applications of UDP are: -
DNS –Domain Name Services
SNMP-Simple Network Management Protocol TFTP – Trivial File Transfer Protocol
RTP – Real Time Protocol
Reason for using UDP instead of TCP
TCP is a complicated protocol involves:
· Flow control
· Exchange of acknowledgements etc.,
· Hence for delay sensitive applications, TCP becomes inefficient; However TCP gives utmost importance for reliability ( but at the cost of efficiency )
· There are many applications which don’t demand reliability, but demand fast delivery
· Typically audio / video streaming applications, where even loosing some bits doesn’t matter
Unit III TCP/IP -1 Question Bank
1. Explain with diagram the TCP/IP architecture (Dec 10 08 M)
2. Explain IPV4 header. (Feb 06, 6M) (July 09, 6M) (Jan 10, 6M)
3. Explain the IP addressing scheme. (Feb 05, 6M)
4. Distinguish between address resolution protocol and reverse address resolution protocol.
(Feb 05, Aug 05, 6M) (July 07, 5M)










Comments
Post a Comment